What Is Hybrid Cloud Security?
Hybrid cloud security is the set of practices, procedures, and technologies used to secure a hybrid cloud environment.
Hybrid cloud security protects data, applications, and infrastructures across a mix of IT environments, including on-premises hardware, private clouds, and public clouds. It must accommodate the unique characteristics of both private and public cloud resources and provide a cohesive security framework to ensure the confidentiality, integrity, and availability of data and applications as customer traffic passes between the environments.
Hybrid cloud is a mixed computing environment that combines compute infrastructure from the public cloud, such as AWS, Microsoft Azure, or the Google Cloud Platform, with an organization’s private cloud or on-premises data center. The primary advantage of a hybrid cloud is agility: Organizations can scale compute resources up and down according to need, and choose where workloads are processed based on requirements for data security, compliance, workload sensitivity, or performance.
The public cloud allows enterprises to host applications and data in shared computing resources owned by a third-party service provider. The public cloud offers access to almost limitless computing resources in a pay-as-you-go model, offering organizations massive economies of scale without the need to invest in data center hardware. The private cloud is dedicated—not shared—cloud infrastructure controlled by the enterprise, and can be operated by a third party co-location provider, or hosted in a private data center and managed by the organization.
Private clouds can offer greater control and more robust security than public clouds, making them better suited for processing or storing sensitive data, or for processing mission-critical applications that require high levels of security, compliance, and customization.
Multi-cloud is another type of cloud, where an organization generally uses multiple cloud computing services from different cloud providers to meet specific business needs and customer demands. Multi-cloud security provides consistent and comprehensive protection for data and applications that are deployed across multiple cloud computing platforms from multiple cloud service providers.
There are key differences between hybrid cloud security and multi-cloud security. Hybrid cloud security focuses on consistently securing resources in public and private clouds. Multi-cloud security, on the other hand, generally refers to the use of services from multiple cloud providers, and requires a broader security strategy to consistently protect against misconfiguration, exploitation, and laterally spreading threats. Hybrid cloud security is therefore a subset of multi-cloud security.
Benefits of Hybrid Cloud Security
A hybrid cloud security model enables organizations to protect sensitive data and applications by keeping them on-premises, while using the public cloud for less sensitive workloads. By separating sensitive data and applications from the public cloud, organizations can better manage security risks, reducing the fallout of data breaches or likelihood of cyberattacks.
This security approach delivers benefits for regulatory compliance, as organizations can keep sensitive or protected data on-premises, while using the public cloud for less sensitive data and workloads. The hybrid cloud security model also allows organizations to use the public cloud as a disaster recovery site in the event of an outage, or to “burst” to the public cloud to handle traffic spikes.
Challenges of Hybrid Cloud Security
Implementing a hybrid cloud security strategy can provide many benefits for organizations, but it also comes with multiple challenges and risks. These include:
- Shared security responsibility: In a hybrid cloud environment, the customer and the cloud provider share the responsibility for security, and it’s important to understand the division of accountability regarding what aspects of security fall to each. Customers must make sure that providers meet their responsibilities, and understand that the customer may need to implement additional security measures to ensure comprehensive security across all cloud environments.
- Incident handling: Incident handling can be challenging in a hybrid cloud environment due to the distributed nature of the infrastructure. It can be difficult to identify the source of an incident and to coordinate the response across different environments. Even if the incident occurs in the provider’s infrastructure, customers may need to work with them to remediate the issue.
- Application security: Hybrid cloud environments can have different application security requirements and configurations, making it a logistical challenge to maintain and secure cloud-based apps. This is especially true for remediation of an application vulnerability exploit that targets a common software library used across the environment.
- Identity and access management (IAM): Managing user identities and access across multiple cloud environments can be complex due to the decentralization of the hybrid cloud and the range of different IAM tools and processes used on different platforms. Additionally, there is an increasing amount of machine-to-machine traffic from APIs and third-party integrations, which necessitate a different approach to identity-based security.
- Compliance and governance: Due to lack of visibility and decentralized management in some cloud environments, which can lead to incomplete logging and forensics, meeting and enforcing compliance and governance requirements can be challenging.
- Security in the supply chain: Cybercriminals can take advantage of multi-vendor hybrid cloud environments because many organizations lack visibility and control over their entire supply chain. Organizations need to ensure that their cloud providers have robust security measures in place and perform regular security audits, penetration tests, and vulnerability scans.
- Data protection: Organizations need to ensure that their data in a hybrid cloud environment is protected both at rest and in transit and that appropriate SSL/TLS encryption and access controls are in place to limit exposure.
- Visibility and control: It can be challenging to maintain visibility and control over security in a hybrid cloud environment, especially when cloud environments are managed separately. Without a centralized dashboard, monitoring, protecting, and troubleshooting security across environments can be arduous, leading to blind spots in security performance and control.
A secure and compliant hybrid cloud environment requires a holistic approach that includes consistent security policies and practices, end-to-end visibility, and strong governance and compliance measures to ensure that organizations can reap the benefits of the hybrid cloud without compromising their security posture.
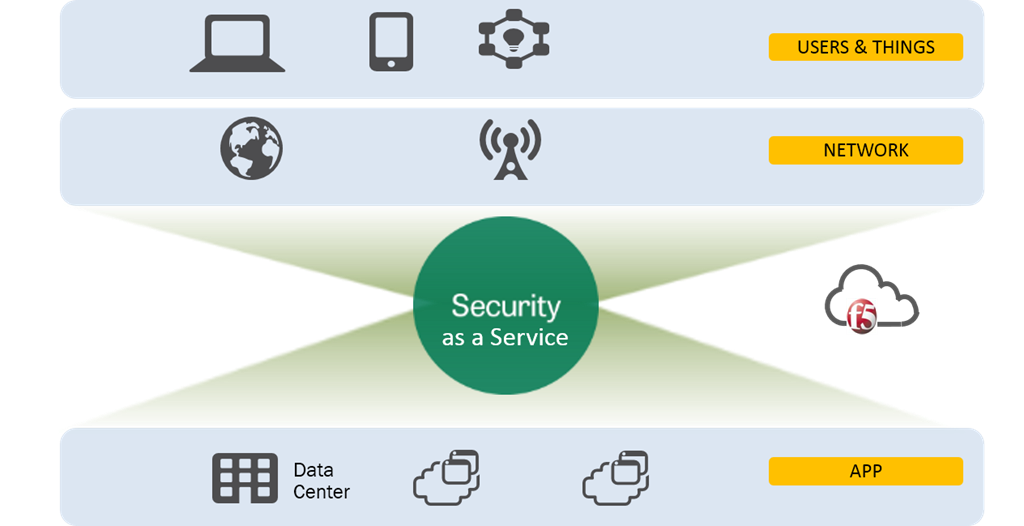
Hybrid Cloud Security Architecture
The architecture for hybrid cloud security includes protection for apps, APIs, underlying infrastructure, and software supply chains. Because data is accessed or otherwise made available through data centers and cloud environments, it must be encrypted to ensure that only valid users and applications can access and use it, typically through some form of zero-trust security model. Zero trust dictates that all requests for access to resources, whether originating from inside or outside the network, must be verified, authenticated, and continually assessed for every request.
At the architecture’s perimeter, edge cloud servers and application containers undergo microsegmentation [insert link to new microsegmentation glossary page], a security technique that involves dividing a network into smaller segments, each with its own security policies and controls, to isolate and protect critical assets from potential security threats. These create “demilitarized zones” or DMZs that restrict access to sensitive data and servers and limit the blast radius of an attack. These DMZs serve as a buffer that allows organizations to expose certain services to the public Internet while keeping the rest of their network secure.
Firewalls add additional layers of protection, further separating cloud environments from on-premises resources.

Components of Hybrid Cloud Security
Hybrid cloud security consists of three components: physical, technical, and administrative.
Physical controls are for securing the actual hardware, while technical controls protect the IT and processing systems. Administrative controls are implemented to account for human actions or natural factors that can impact security.
Physical Controls
Physical controls are a vital aspect of hybrid cloud security, as they safeguard the physical infrastructure that supports the hybrid cloud environment. Hybrid clouds can span multiple locations, which makes physical security both a special challenge and a critical responsibility.
Physical controls include access restrictions to data centers, server rooms, and other areas that contain critical infrastructure. Surveillance systems like CCTV cameras, motion detectors, and monitoring systems to monitor access to critical infrastructure and detect any unauthorized activity are also considered physical controls.
In addition, physical controls can include backup power systems like an uninterruptible power supply (UPS) and backup generators to ensure that the hybrid cloud environment remains operational during power outages.
Organizations should develop service level agreements (SLAs) with cloud providers to define how physical security standards will be met.
Technical Controls
Technical controls are critical to hybrid cloud security, and include:
- Encryption, which is used to protect data in transit and at rest. SSL/TLS encryption ensures that data is protected even if it is intercepted by unauthorized users.
- Automated provisioning and configuration, which helps organizations reduce the risk of human error and ensure consistent and efficient security management across their hybrid cloud environment.
- Orchestration, which automates the coordination of different security tools, systems, and processes to ensure that they work together seamlessly to protect the hybrid cloud environment.
- Access control, which involves implementing policies and procedures to ensure that only authorized users are able to access sensitive data and applications hosted in the hybrid cloud environment. Zero trust principles including least privileged access are increasingly important in hybrid cloud environments.
- Endpoint security, which prevents unauthorized access from misplaced, stolen, or compromised devices such as laptops and mobile phones by purging device data or revoking access to the data center.
Administrative Controls
Security is every user’s responsibility, and administrative controls help people act in ways that enhance security.
Organizations should provide training and awareness programs for employees, contractors, and other users of the hybrid cloud environment. This training should cover topics such as cloud security best practices, data classification, access control, and incident response, and should be tailored to the specific roles and responsibilities of each stakeholder.
Hybrid cloud architecture offers significant advantages for data recovery and disaster planning and preparedness. Because hybrid clouds involve both private and public clouds, organizations can employ the public cloud as a failover for on-premises data and applications, enabling backups, redundancy, and disaster preparedness and recovery scenarios.
Hybrid Cloud Security Best Practices
Hybrid cloud security is complex and requires careful planning, implementation, and ongoing management. Here are some best practices to consider as organizations begin developing their approach to hybrid cloud security.
- Data classification and protection. Classifying data based on its sensitivity and criticality helps organizations determine how to store, transmit, and access the data, and what security measures to apply. Implementing appropriate data protection measures such as encryption, access controls, and backup and recovery processes is also critical for ensuring that data is protected as it transits the hybrid environment.
- Access control and identity management. Organizations should implement strong access controls and identity management processes, role-based access controls, and privilege management, to ensure that only authorized users and applications can access sensitive resources. Zero trust principles can help protect modern workloads from sophisticated attacks that target weakness in authentication and authorization
- Network security and segmentation. Network security is also critical in a hybrid cloud environment, where resources are distributed across multiple locations and providers. Implementing strong security measures such as network firewalls, web application firewalls, cloud workload protection platforms, and network segmentation is critical for ensuring that traffic is restricted only to authorized users and applications.
- Encryption and key management. Encryption protects data in transit and at rest in a hybrid cloud environment, and must be implemented throughout the data lifecycle. Encryption keys must also be carefully protected to ensure that only authorized users and applications can access them, or the encrypted data.
- Continuous monitoring and incident response. Continuous monitoring of security events and logs is necessary to identify potential threats and respond quickly to security incidents. Organizations must have an incident response plan in place that outlines roles and responsibilities, incident escalation procedures, and communication protocols.
Hybrid Cloud Compliance and Governance
Managing compliance and governance in a hybrid cloud environment can be challenging, and includes the following considerations.
- Regulatory compliance. For organizations that operate in regulated industries, such as healthcare, finance, and government, regulatory compliance in a hybrid cloud environment is a critical concern. Organizations must identify the regulations that apply to their industry, evaluate their existing infrastructure and processes, and implement the necessary controls to meet requirements. This may include data encryption, access controls, and audit logs to demonstrate compliance.
- Data privacy and protection. Since sensitive data may be stored in multiple locations in hybrid cloud environments, including public cloud infrastructure, data privacy and protection are major considerations in hybrid cloud environments. Organizations must establish clear data protection policies, identify the locations of sensitive data, and implement encryption and access controls to prevent unauthorized access to sensitive data.
- Risk management and mitigation. Organizations must conduct regular risk assessments to identify potential threats and vulnerabilities. This helps pinpoint and address the possible threats to the infrastructure and quantify the damage they might cause. Evaluate alternative solutions to avoid or mitigate risks, implement the appropriate security controls, and monitor the environment for security incidents.
- Incident response planning. Security incidents can have a significant impact on business operations and reputation. Organizations must develop a comprehensive incident response plan that outlines the steps to be taken in the event of a security incident, including procedures for detecting and reporting, containing and isolating the incident, investigation, and restoring operations.
- Vendor management: Vendor management is a critical aspect of hybrid cloud compliance and governance since organizations rely on third-party cloud service providers to manage their infrastructure and applications. To manage vendor risk in a hybrid cloud environment, organizations must conduct due diligence on potential vendors, establish clear SLAs that outline the vendor's responsibilities and obligations, and monitor the vendor's performance regularly to ensure compliance with regulatory requirements.
Tools and Technologies for Hybrid Cloud Security
Following are solutions, services, and tools to consider when evaluating and selecting features for hybrid clouds.
Hybrid Cloud Security Solutions
- Data loss prevention (DLP) is a security solution that monitors and prevents sensitive data from being accessed, exfiltrated, or transmitted in unauthorized ways. DLP provides policy-based controls to manage and protect data across on-premises data centers, cloud environments, and endpoint devices. Web application firewalls provide flexible and performant defenses to prevent sensitive data loss.
- Network security solutions protect networks against unauthorized access, attacks, and other security threats through a combination of controls, including firewalls, intrusion detection and prevention systems, analytics, and other security technologies to protect incoming and outgoing traffic on networks.
- Vulnerability management is a proactive, automated solution that scans and assesses IT infrastructure for potential security threats and weaknesses, and provides remediation recommendations. Vulnerability management should be a continuous process to keep current with new and emerging threats. Web application firewalls can provide a critical stopgap to mitigate potentially devastating application vulnerability exploits.
- Threat intelligence and detection systems collect and analyze data from multiple sources and use machine learning and other analytic techniques in addition to research and oversight from Security Operations Center (SOC) staff to identify and mitigate emerging and pervasive security threats.
- Compliance management solutions track and report on compliance requirements, and help organizations avoid penalties and other risks associated with non-compliance.
Hybrid Cloud Security Services
- Cloud security assessment services provide recommendations for improving security controls and mitigating risks by evaluating the security posture of cloud environments to identify risks and vulnerabilities.
- Cloud security management is a service that provides centralized visibility and controls over security policies and configurations by monitoring security features in cloud environments.
- Cloud encryption services encrypt data in transit and at rest in cloud environments, and also provide key management and access controls to ensure secure data protection.
- Cloud workload protection platforms secure underlying infrastructure such as container images, authentication keys, and software supply chains, and also protect against privilege escalation, lateral movement, and data exfiltration.
- Identity and access management (IAM) provides authentication, authorization, and access control services to ensure secure and compliant access across multiple cloud environments. The rise of machine-to-machine traffic from APIs and third-party integrations necessitates new identity-based security approaches.
Tools for Hybrid Cloud Network Security
- Virtual private networks (VPNs) provide a secure tunnel between a user's device and the network they connect to, enabling remote encrypted access to cloud resources. VPNs can be used to securely connect public and private clouds and extend private networks across public clouds to secure data traffic in hybrid environments.
- Firewalls are used to control access to a network by monitoring and filtering traffic based on predefined rules. They can be implemented at the perimeter of the network, between different cloud environments, and within each cloud environment.
- Intrusion detection and prevention systems (IDPS) are designed to detect and prevent security threats by analyzing network traffic and identifying malicious activity. They can be deployed in a hybrid cloud environment to monitor and protect cloud resources from attacks such as DDoS, malware, and phishing.
- Security information and event management (SIEM) solutions provide real-time monitoring and analysis of security events across an organization's hybrid cloud infrastructure. SIEM tools can collect and aggregate log data from different cloud environments and correlate events to identify potential security threats.
- Secure Socket Layer (SSL) and Transport Layer Security (TLS) are cryptographic protocols used to secure communications over the Internet. SSL and TLS can be used to encrypt data in transit between cloud environments, ensuring that sensitive information is protected from interception and tampering.
Future of Hybrid Cloud Security
Here are some emerging trends in hybrid cloud security, pointing to how it may evolve in the coming years.
- Zero-trust security assumes there is no traditional network edge, and considers all network traffic to be potentially malicious. Zero trust security requires all users, whether in or outside the organization’s network, to be authenticated, authorized, and continuously validated before being granted access to protected applications and data. This security approach involves implementing strong access controls, authentication, and authorization processes, and continuous monitoring of network traffic to detect and respond to potential threats.
- Cloud-native security is an approach to hybrid cloud security that leverages cloud-specific tools and technologies to improve security. This approach incorporates security into an organization's overall cloud-native application development strategy and includes container security, microsegmentation, and serverless security, as well as cloud-based threat intelligence and security analytics.
- Edge security becomes an important consideration as more organizations adopt edge computing to process data closer to its source. Edge security involves implementing security controls and monitoring at edge devices and gateways and ensuring secure communication between edge devices and the cloud.
Hybrid cloud has already proven to be a game-changing technology for many businesses, providing them with the flexibility, scalability, and cost savings they need to stay competitive. But securing the hybrid cloud can be complex and requires the right hybrid cloud security strategy to ensure that sensitive data and workloads are protected at all times.
To help simplify your hybrid cloud strategy, F5 offers a comprehensive set of security and management tools that remain consistent across clouds and protects data and applications across multiple IT environments.



